Prerequisites
To follow this guide, you’ll need:- An Okta account with the following permissions:
- An existing Superblocks SSO configuration using Okta OIDC
- A REST or GraphQL-based backend API
If your Superblocks SSO currently uses a SAML-based flow, please reach out to our support team for assistance migrating to an OIDC-based log-in flow
Token exchange flow
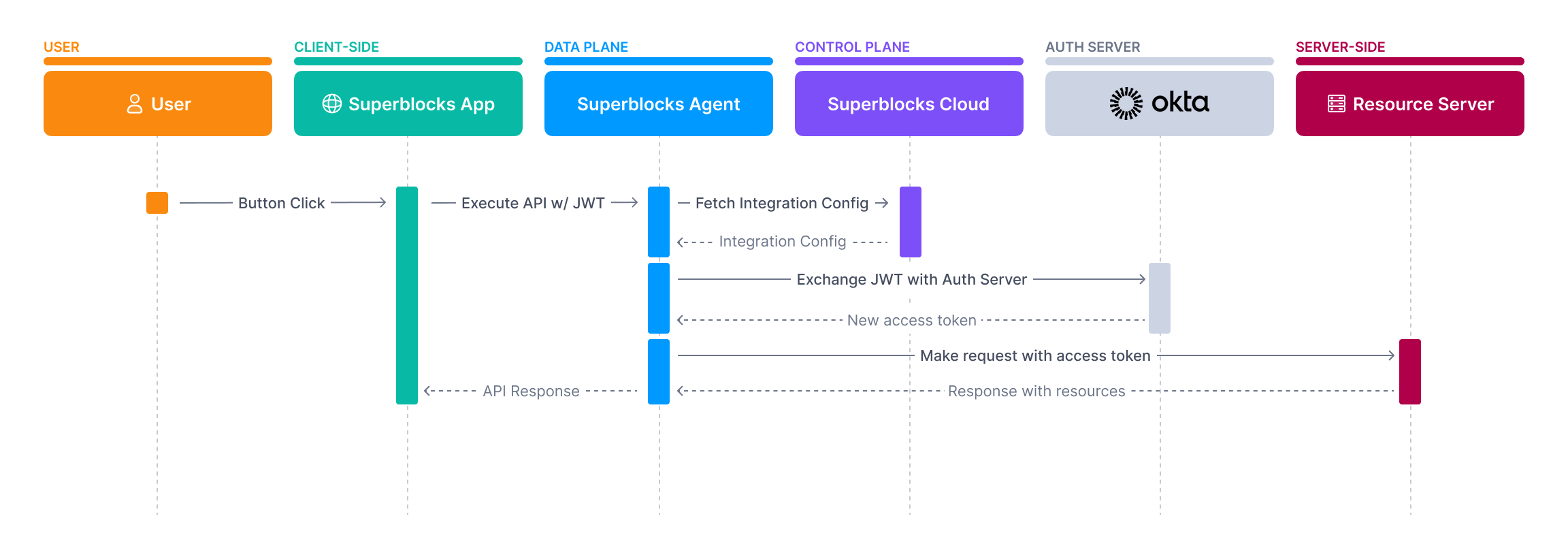
Note: This flow assumes the user is already logged into Superblocks
- Your user will log in to Superblocks using your Okta OIDC app
- When the user executes an API, a request is sent from the browser to the Superblocks Agent that includes the user’s Okta JWT
- The API includes a step to make a request to your backend API. The Superblocks Agent will make a request to your Okta authorization server to exchange the user’s Okta JWT for a new token intended for your backend API
- The Okta authorization server validates the user’s JWT and then grants a new access token with scopes that allows Superblocks to make requests to your backend API. The new access token retains the user context so your backend API knows on whose behalf the request is made.
- The Superblocks Agent makes a request to your backend API and includes the new access token
Setup instructions
The following instructions show how to configure Okta & Superblocks to perform the token exchange.Create an API in Okta
To perform the token exchange, you’ll need to create an API application that the Superblocks Agent will use to act as an OAuth client for your backend API.- Log in to Okta and go to the Admin Console
- Navigate to Applications → Applications
- Click Create App Integration
- Select API Services followed by Next
- Name the app something like Superblocks Integration and click Save
- Click Edit in the General Settings section of the General tab
- Uncheck the checkbox for Require Demonstrating Proof of Possession (DPoP) header in token requests
- Check the checkbox for Token Exchange and click Save
- Make a note of the
Client IDin the Client Credentials section and theClient Secretin the CLIENT SECRETS section
Create an authorization server
During the token exchange, the Superblocks Agent exchanges the user’s OpenID access token granted during log in with an Okta Authorization Server configured to issue tokens for our backend API.Create the authorization server
- In the Admin Console, go to Security → API
- On the Authorization Servers tab, click Add Authorization Server
-
Enter a Name, Audience, and Description for the authorization server
Note: The Audience value specified will be set as the
audclaim of the access token sent to your backend API. The Audience property should be set to the URI expected by your API.
Add custom scopes & claims
- From the authorization server, select the Scopes tab
- Click Add scopes and add any custom scopes your backend API requires
- Click on the Claims tab
- Click Add claim and configure any custom claims you want to include on the access token
Create access policies and rules
- From the authorization server, select the Access Policies tab and click Add Policy
-
In the Add Policy dialog that appears, enter the following:
- Name: Access Superblocks
- Description: Enter a description
- Assign to: Select The following clients and search for your organization’s Superblocks SSO application
- Click Create Policy
-
Click Add Rule and in the dialog that appears, enter the following:
- Name: Superblocks App to Agent
- AND Scopes requested: Select The following scopes and enter
openid
- Click Create rule
-
Repeat steps 1 - 5 to create a policy and a rule that lets the Superblocks Agent talk to your backend API.
Use the following values for the policy:- Name: Access Backend API
- Assign to: Select The following clients, start typing the name of the API that you created earlier
- Name: Agent to Backend API
- AND Scopes requested: Select The following scopes, and select any of the custom scopes you configured previously
- AND Refresh token lifetime is: Unlimited (this is recommmended but not required)
Update SSO metadata
Superblocks SSO by default uses your Okta Org Authorization Server. To use token exchange, we’ll need to update your SSO configuration to use a Custom Authorization Server. To do this, we will need the.well-known/openid-configuration URL of your Authorization Server.
To locate this URL:
- Go to the Settings tab of your Authorization Server
- Copy the Metadata URI shown in the Settings section
- Replace
oauth-authorization-serverwithopenid-configuration - Send this link to support@superblocks.com with the Subject Update Okta SSO to use Token Exchange
If your backend uses a micro-services architecture that has multiple APIs, or you plan on using token exchange for your backend API as well as services like Snowflake, make sure you’ve added this server as a trusted server to all other auth servers you’ll use in Superblocks.
Update your integration
Once you’ve gotten confirmation from Superblocks that we’ve updated your SSO to use the new Authorization Server, you’re ready to configure your Integration. To do so:- Navigate to the Integrations page and search for your REST or GraphQL API
- Select OAuth2 - On-Behalf-Of Token Exchange as the Authentication method
- Choose Login Identity Provider as the Subject token source
-
Specifying the following configuration values:
Field
Required Description Token URL ✓ The token_endpointfound in your Authorization Server’s{SERVER}/.well-known/oauth-authorization-servermetadata fileClient ID ✓ The client_idof the API created earlierClient secret ✓ The client_secretof the API created earlierAudience ✗ Your Authorization Server’s Audience Scopes ✗ Any custom scopes you configured for your authorization server -
Use the
oauthobject in Headers or Params to define how the access token returned by the authorization server should be sent to your API
Okta Authorization Servers can only return an
access_token, not an id_token. For this reason, oauth.idToken and oauth.tokenDecoded aren’t available when using this auth method.Testing & troubleshooting
Test your integration
With your integration updated to use your Okta authorization server to issue access tokens, you’re ready to test it in a Backend API.- In an Application create a new Backend API
- Add a step that uses your Integration
- Configure the step to make a request to your API
- Click Run API
Troubleshooting
The easiest way to troubleshoot authorization issues is by inspecting the access token that Superblocks is sending to your API. To do this:- Make a copy of your Integration
- Replace the Base URL with a API resting service like webhook.site or Postman Echo
- Add an Authorization header with the value
{{ oauth.token }} - Save the Integration
- Build a Backend API that uses this “echo” integration
- Run the API and copy the access token from the authorization header
- Use a tool like JWT to inspect the token
Common errors
See the below guide for known error conditions, why they happen, and how to address them.Error message | Why it’s happening | Resolution |
|---|---|---|
Could not find identity provider token | Your organization either doesn’t use SSO or it’s configured in a way that doesn’t support token exchange | Follow docs to set up Okta SSO or contact support@superblocks.com to update your configuration |
Identity provider token expired | Your Okta session has expired so the authorization server won’t issue an access token | Refresh your browser, you should be prompted to reauthenticate. If you’re not, log out and back in. |
Could not find a user JWT | The Superblocks Agent doesn’t have a user JWT so can’t extract a subject_token to send to Okta. It most likely is occurring because the integration is being used in a Workflow, Scheduled Job, or public App. | Refactor your code to use the Integration in a Backend API |
Token exchange failed | Superblocks couldn’t successfully complete the token exchange with the Okta authorization server. | See the additional error details provided by Okta. You may also be able to find additional error information in your Okta system logs. |

