Connection method
When connecting to databases in Superblocks, you will typically have two options:Connection form
This method lets you connect by filling out a simple form with your database credentials. This user-friendly interface is designed for ease of use, enabling you to connect to your database quickly without needing extensive technical knowledge. Connection forms usually limit you to connecting viausername/password authentication. If you need to need to connect using a more advanced authentication method provided by your database, you may want to explore using a connection string.
Connection string
Alternatively, you can connect using a connection string, which lets you enter an arbitrary connection URI. This method provides greater flexibility, letting you specify additional parameters, making it suitable for advanced configurations or custom setups. The format required for the connection string and options available varies by database. The following databases support connection strings and have the following expected forms. Database | String format | Docs |
|---|---|---|
| Amazon Redshift | redshift://[:username]:[:password]@[:host]:[:port]/[:database] | Docs Note: Exclude the jdbc prefix from the connection string |
| CockroachDB | postgres://<username>:<password>@<host>:<port>/<database>?<parameters> | Docs |
| MariaDB | mariadb://[<user>[:<password>]@]<host>[:<port>]/[<db>[?<opt1>=<value1>[&<optx>=<valuex>]]] | Docs |
| Microsoft SQL | Server=[:serverName],[:port];Database=[:database];User Id=[user];Password=[:password];Encrypt=[true/false] | Docs |
| MongoDB | mongodb+srv://<username>:<password>@<host>/?retryWrites=true&w=majority | Docs |
| MySQL | mysql://[:username]:[:password]@[:host]:[:port]/[:database] | Docs |
| PostgreSQL | postgres://[:user]:[:password]@[:host]:[:port]/[:database] | Docs |
| Redis | redis://[:password@]host[:port][/db-number] | Docs |
Networking
For Superblocks to connect to your database the Superblocks Agent will need network access. If you database is available on public subnets or allows any IP to connect, you should have no problems. For security purposes, many databases are configured to limit who can connect to them. In this case, you’ll need to configure you database to accept inbound traffic from the Superblocks Agent.IP allowlist
To let Superblocks Cloud connect to your database, update your database’s ingress allowlist to include the following:- US Region
- EU Region
-
NAT hostname:
nat.superblocks.com - Current DNS: A Records
-
Last recorded IPs:
In-network Agent
Alternatively, you can access in-network resources by deploying the Superblocks data plane inside the same network as your database. The data plane service will execute your APIs and connect directly to your databases, ensuring all your data is kept securely within your corporate firewall.Network settings
SSL configuration
Superblocks supports the ability to establish connections using Secure Socket Layer (SSL), a protocol for creating authenticated and encrypted links between networked computers.Configuring SSL
SSL can be configured using the Integration configuration form for supported integrations.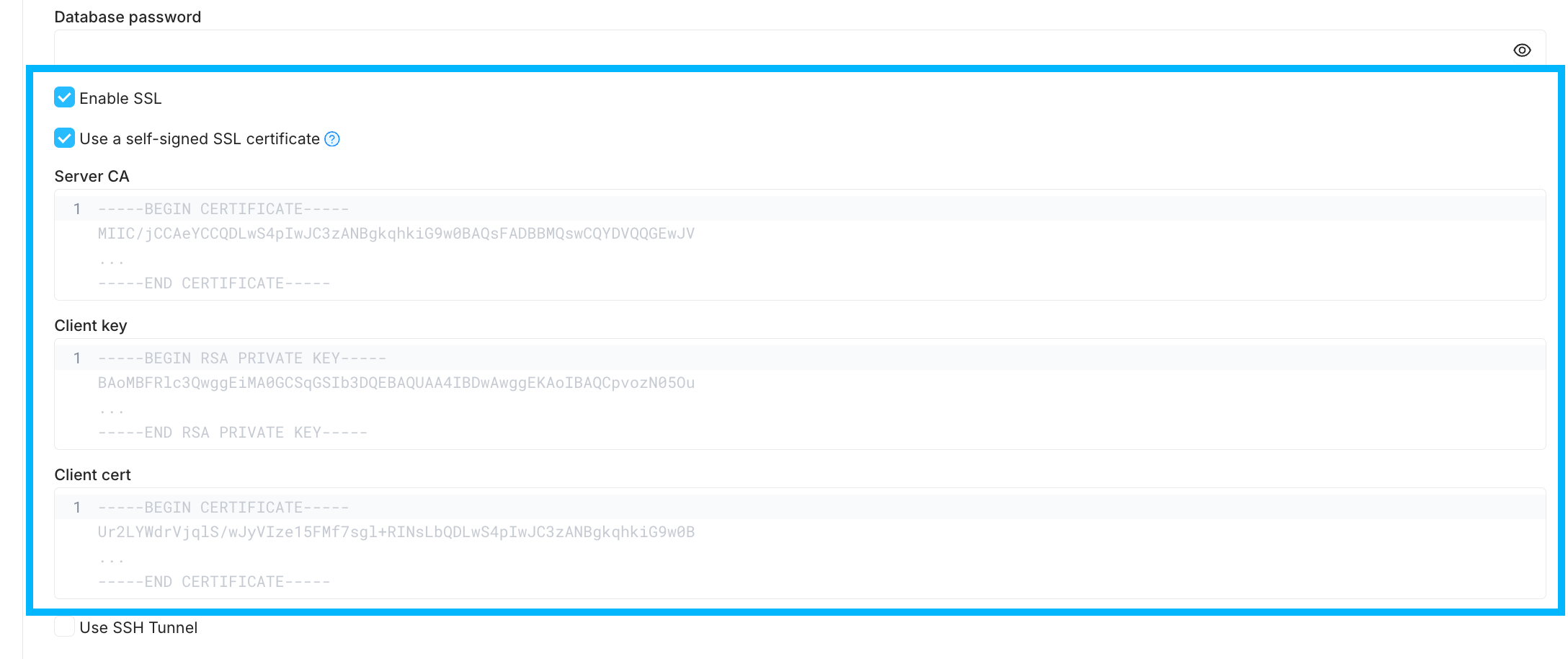
- On the Integration configuration form for your DB, select Enable SSL
- Optionally, select Use a self-signed SSL certificate. If selected, provide the following:
- Server CA: Database server’s Certificate Authority (CA) certificate
- Client key: Client’s private key
- Client cert: Client’s public key certificate
SSH configuration
SSH Tunneling is only available when using Superblocks Cloud
SSH authentication methods
Superblocks supports the following SSH Authentication methods:- Username/password
- Private key authentication
- Public key authentication (RSA or Ed25519)
Configuring SSH tunnels
SSH tunneling can be configured using the Integration configuration form for supported integrations.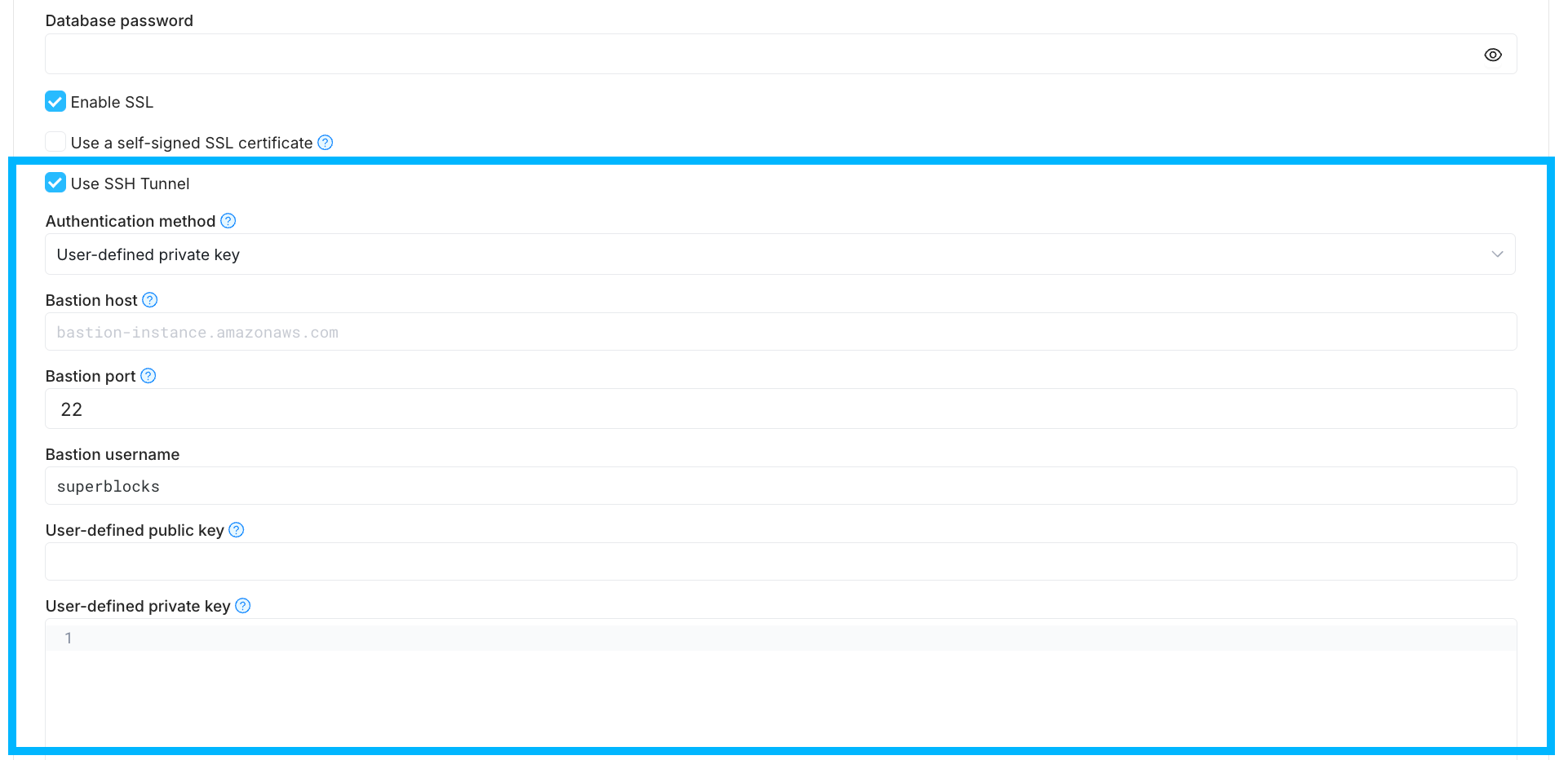
- Configure your SSH server to allow connections from Superblocks’s IPs
- On the Integration configuration form for you DB, select Use SSH Tunnel
- Select an Authentication method
-
Specify the following shared configuration values:
- Bastion host: The name or IP address of the SSH server
- Bastion port: The port number used for the SSH connection
- Bastion username: The username required for SSH authentication
-
Follow instructions based on the selected Authentication method
- Password
- Private key
- Public key (RSA or Ed25519)
Enter the following configuration values:- Password: The SSH account password for the Bastion user
Support by Integration
The following network settings are supported by each database integration.| Integration | SSL | SSL Certificate | SSH Tunneling |
|---|---|---|---|
| Amazon Redshift | ✓ | ✗ | ✗ |
| CockroachDB | ✓ | ✓ | ✗ |
| MariaDB | ✓ | ✓ | ✗ |
| Microsoft SQL Server | ✓ | ✗ | ✗ |
| MongoDB | ✓ | ✓ | ✗ |
| MySQL | ✓ | ✓ | ✓ |
| Postgres | ✓ | ✓ | ✓ |

