Superblocks Hybrid is designed for organizations that require production data and application execution to remain entirely within their AWS, GCP, or Azure environment, while offloading platform management and control plane operations to the Superblocks cloud. With Superblocks Hybrid, the Superblocks control plane and AI inference for development are hosted and managed in the Superblocks cloud, while the data plane is deployed inside your cloud provider VPC, directly colocated with your private production data. All production code executes locally within the customer network, ensuring production data never leaves customer-controlled boundaries. This model gives customers strong guarantees around production data residency, network isolation, and execution locality, while Superblocks manages the platform lifecycle—including upgrades, reliability, and operational support. The result is enterprise-grade security and control without the operational burden, slow iteration cycles, or complexity of a fully self-hosted deployment.
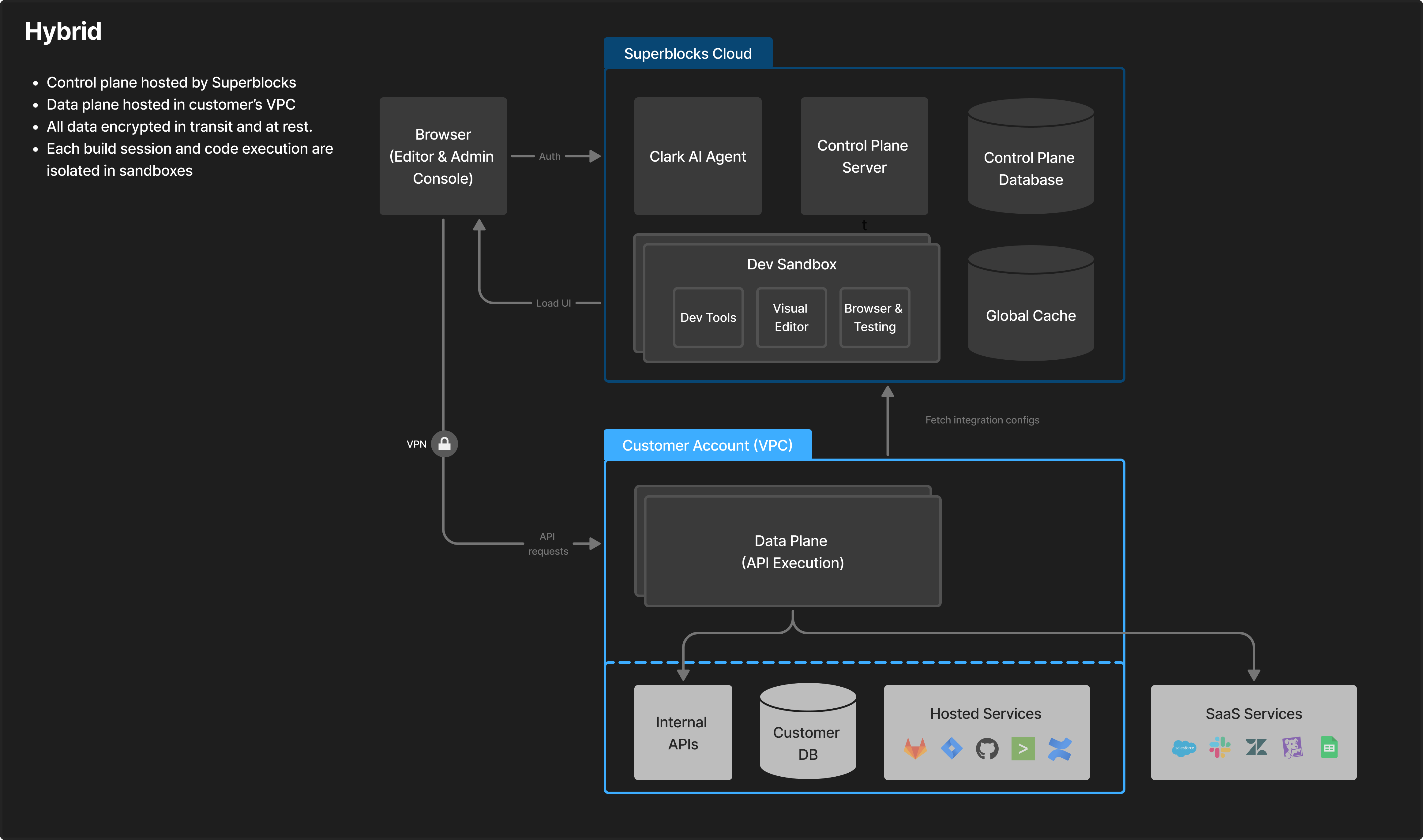
Hybrid architecture - Edit mode
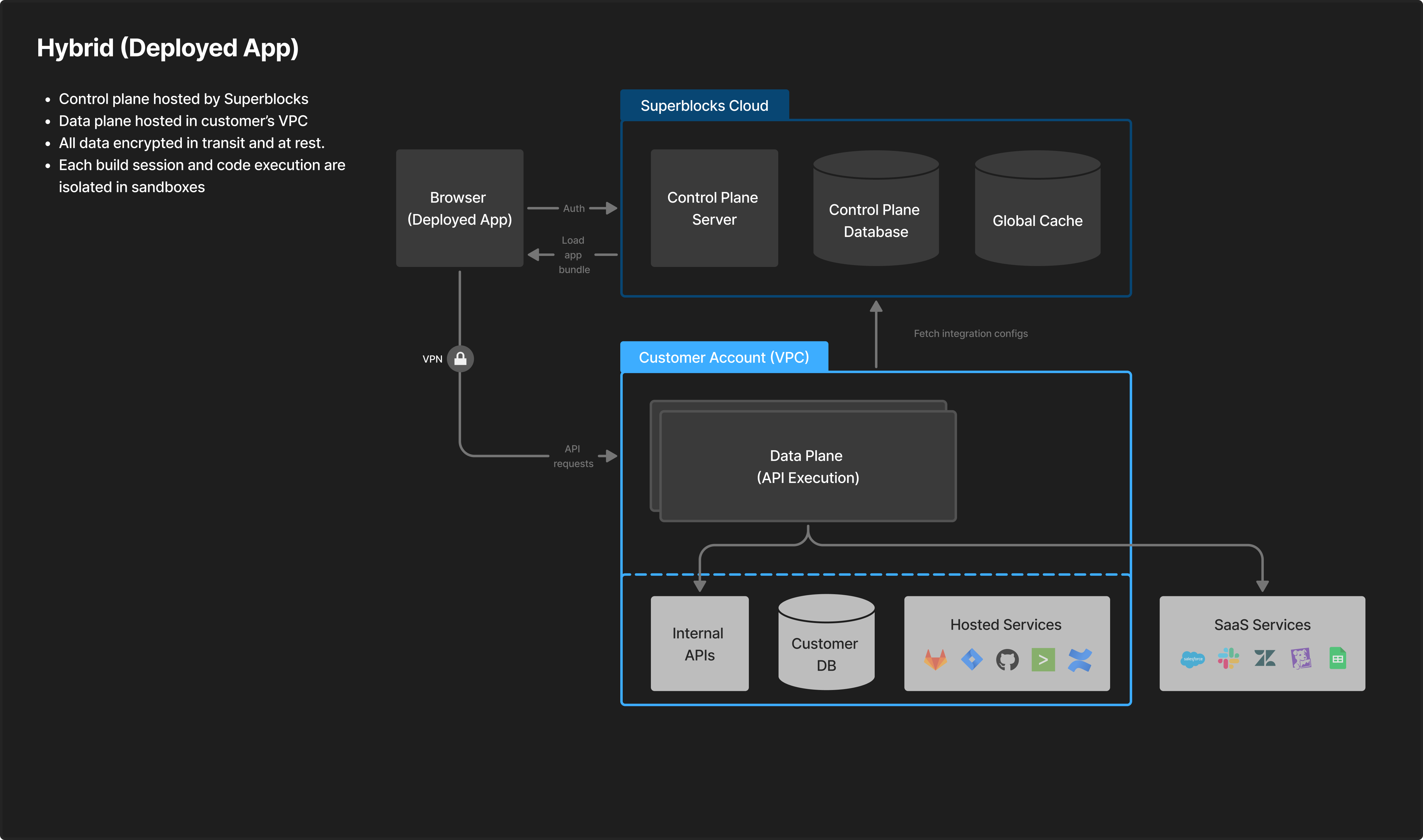
Hybrid architecture - Deployed mode
How it works
In the Superblocks Hybrid deployment model:- Cloud-hosted control plane and AI: The Superblocks control plane—and AI inference for development and non-production workflows—run in the Superblocks cloud and are fully managed by Superblocks.
- Private, single-tenant data plane: A dedicated Superblocks data plane is deployed inside your AWS, GCP, or Azure VPC and executes all production application APIs locally.
- Production data stays in your network: Deployed applications connect directly to the data plane for secure, low-latency access to private APIs, databases, and internal services, with production data never leaving the customer VPC.
- Outbound-only connectivity: The data plane communicates outbound-only to the control plane, requiring no inbound network access or exposed firewall ports.
- Enterprise identity and managed operations: Access is governed by your enterprise SSO and centralized Superblocks RBAC, while Superblocks operates and supports the platform end-to-end, including upgrades, reliability, and ongoing support.
Why choose Hybrid
Superblocks Hybrid is best for enterprises that require private network execution and data locality, but want to avoid the operational overhead and cost a cloud-prem:- Private, high-performance production execution: All production application APIs, workflows, and data access execute locally inside your AWS, GCP, or Azure VPC—behind existing network controls—delivering low-latency, predictable performance with production data never leaving customer-managed boundaries.
- No inbound network exposure: The data plane communicates outbound-only to Superblocks’ cloud, eliminating the need to open firewall ports or allow inbound connections into your VPC.
- Cloud-hosted AI for development speed: AI inference for edit mode, previews, and non-production data runs in the Superblocks cloud, enabling fast iteration and AI-assisted development without exposing production data.
- Centralized governance without overhead: Control plane services—including configuration, orchestration, RBAC, and audit logs—are managed centrally by Superblocks, providing enterprise-grade governance without operating control plane infrastructure.

