- Public: anyone can view your app, no login required
- Private: users log in to Superblocks directly and must have
apps:viewpermission to the application - SSO: use your application’s existing login flow so users only have to log in once to access the embedded Superblocks app
SSO authentication flow
With SSO embedding, users access your embedded app without needing a separate Superblocks login. Instead, you’ll log users in with your app’s existing auth and issue them a Superblocks session token for embedded auth. Using the Superblocks session token, your user’s identity, level of access, and metadata are securely transmitted to Superblocks so they can’t be modified by users client-side. The following diagram illustrates the authentication flow for SSO embed users: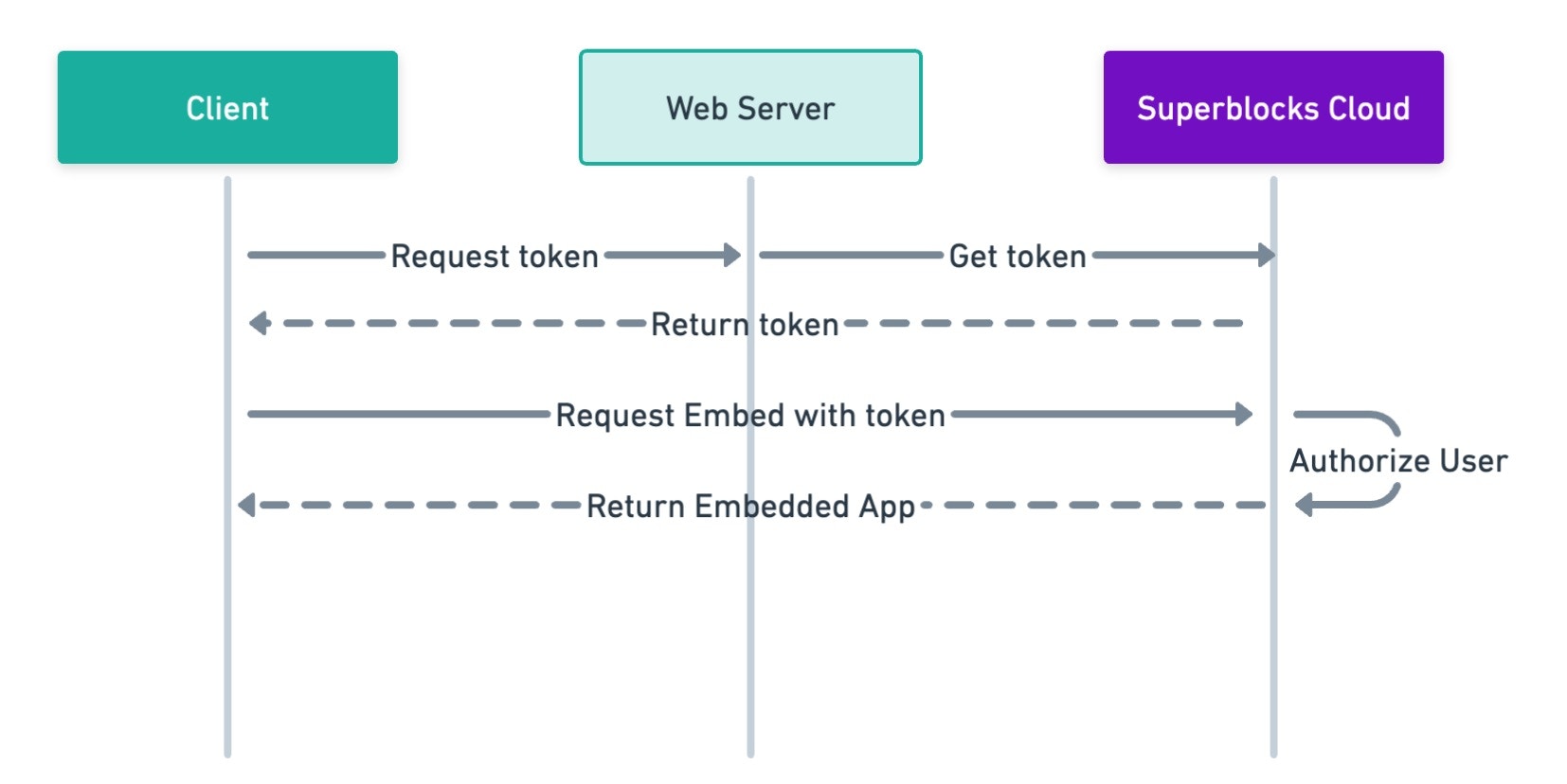
Set up embedded SSO
Use the following instructions to have your application authenticate users with Superblocks.Step 1. Generate an access token
Only organization Admins can create Embed access tokens.
-
Click your avatar in the upper-left corner of the home page and click Organization Settings
- In the left sidebar, click Access Tokens
- Click +Create token
- In the Name field give your token a descriptive name
- Select an Expiration date, or use the default 90 day expiration.
-
Select Embed as the token type
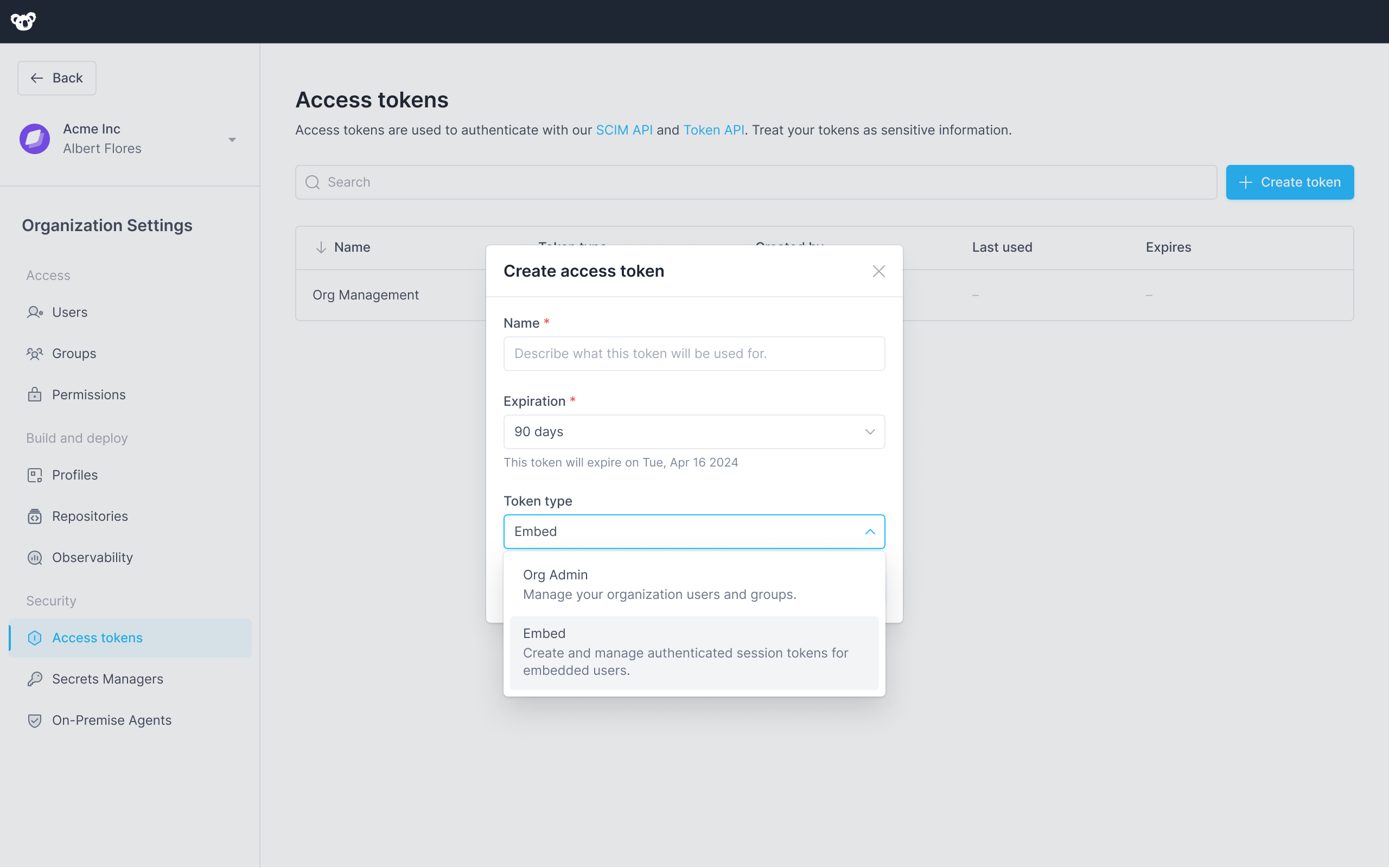
- Click Create
Save your tokens immediately
Your access token is visible one time, immediately after you create it. If you leave or refresh the page where the token is displayed, it will be obscured and no longer visible. You must copy and store new access tokens somewhere secure before you leave the creation page, or you will lose access to the token.
Step 2. Add token endpoint to your web-server
Add an endpoint to your web-server that requests user session tokens from Superblocks. You can add this as a new endpoint, or to your existing authentication flow.- Node.js (Express)
- Python (Flask)
- Django
server.js
Make sure your web server has CORS enabled if it’s running on a different domain than your host application.
For a detailed explanation of the parameters, request format, and response format for the
/token endpoint, please refer to the full API specification below.Step 3. Request token client-side
Add code to your web application to request a session token from the token endpoint you just added to your application’s web server.- React
- JavaScript
src/utils.tsx
Step 4. Pass the token to your embed
- React
- JavaScript
src/views/embed_page.tsx
Manage user access
Embed users must have theapps:view permission to the Superblocks app they’re trying to access.
Grant users access by associating them with a Group with the necessary access level. To associate an embed user with a group:
- Click your avatar in the upper-left corner of the home page
- In the menu, click Organization Settings
- In the left sidebar, click Groups
- Either select + Add group or click into an existing group
-
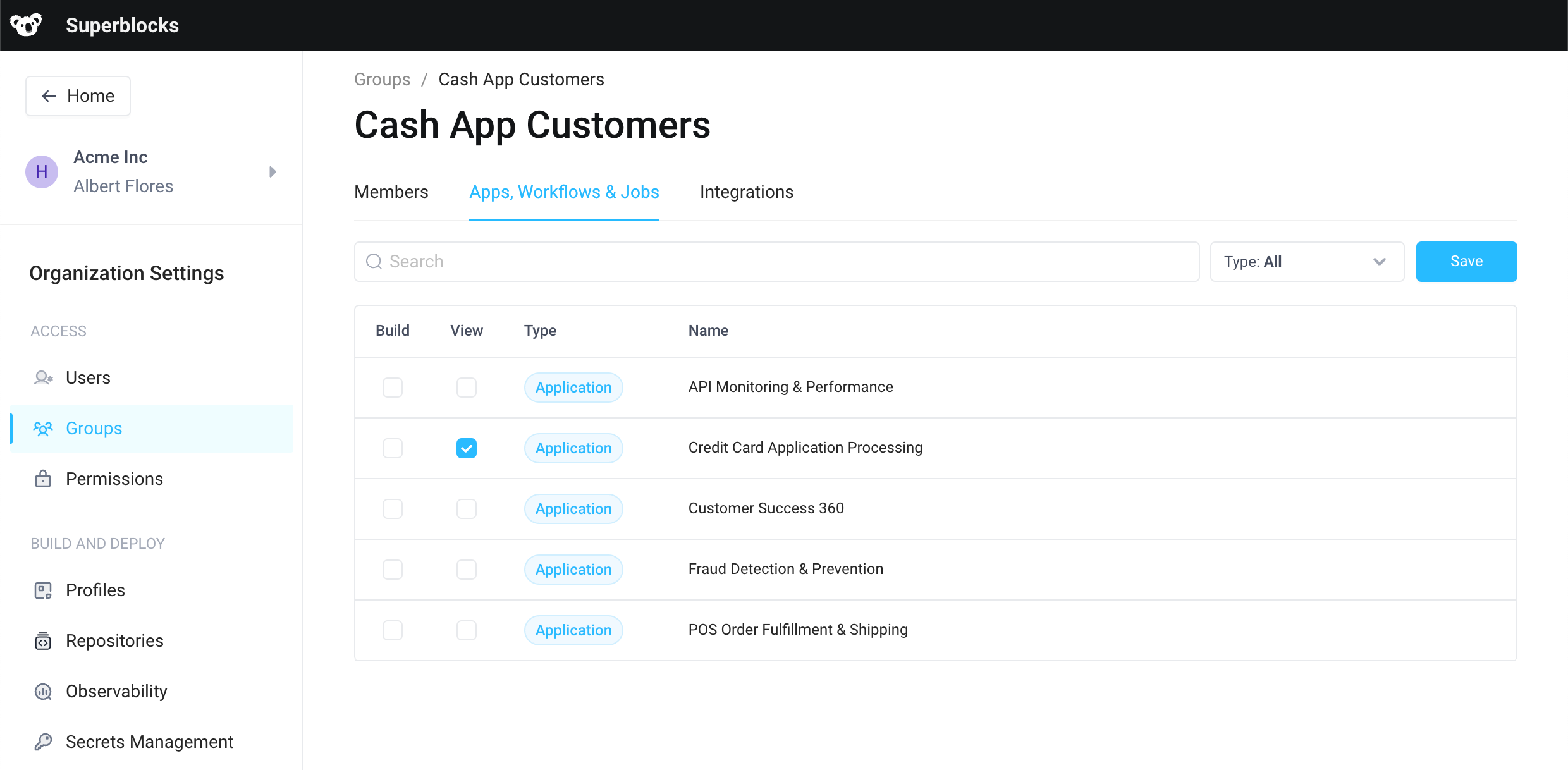
On the Permissions tab, enable View access for apps you want the user(s) to have access to
-
Go back to the Groups page and copy the group’s ID by selecting … → Copy group ID
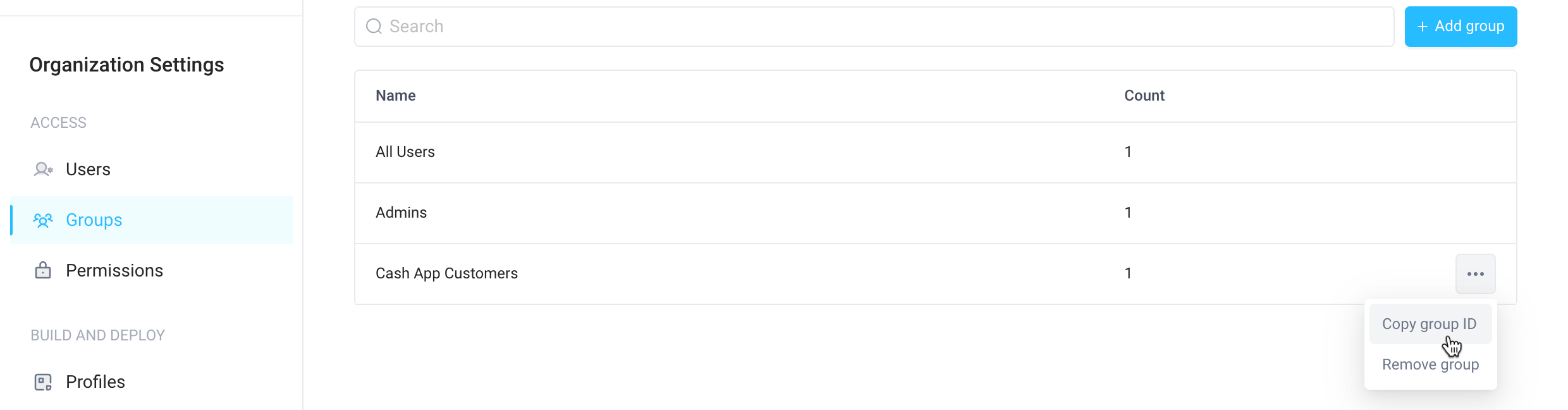
-
Update your server endpoint by adding a list of
groupIdsyou want users to be associated with
- Node.js (Express)
- Python (Flask)
- Django
Customize user metadata
User metadata lets you attach additional information to a user beyond the standard attributes. This can be useful for storing extra data relevant to your application or business logic. To customize user metadata, include ametadata field in your request payload with JSON representing the metadata you want to add. For example:
- Node.js (Express)
- Python (Flask)
- Django
isAdmin metadata attribute
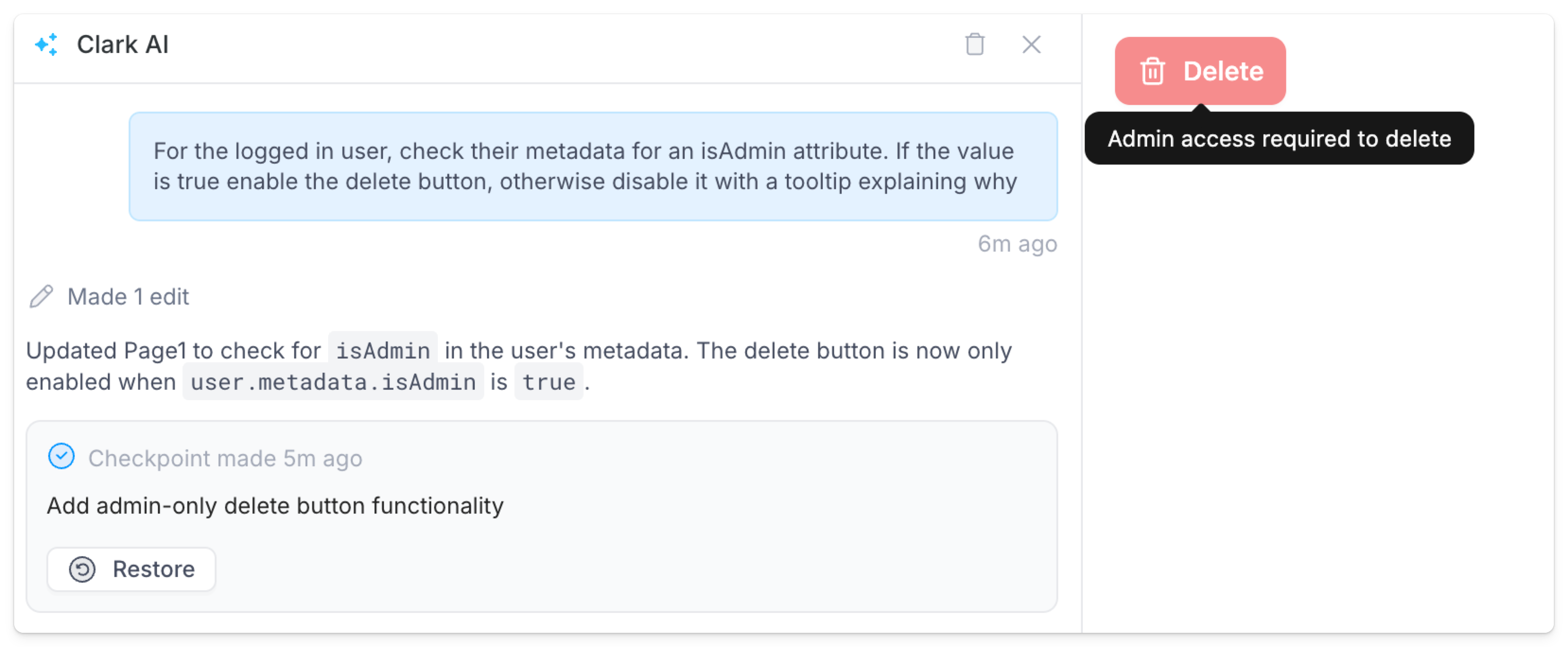
useSuperblocksUser() function to get the logged in user and check their metadata. Here is the code generated from the prompt above.
index.tsx
Token API specification
POST /api/v1/public/token
Use this endpoint to request a session token for an embedded user.
Request parameters
application/json
| Parameter | Required | Type | Description |
|---|---|---|---|
email | ✓ | String | The user’s email address, which uniquely identifies them in Superblocks. |
name | String | The user’s full display name. | |
groupIds | Array | Superblocks Group IDs to associate the embed user with. | |
metadata | Object | Object containing additional metadata about the user. | |
isSuperblocksUser | Boolean | If TRUE, the token will be associated with the Superblocks platform user with the email specified. If no platform user exists with that email, the user will get an Unauthorized error. | |
subject_token_type | String | The type of token being passed in subject_token. Required when using subject_token. Must be set to urn:ietf:params:oauth:token-type:access_token. See On-Behalf-Of Token Exchange for more details. | |
subject_token | String | An access token from an external identity provider (e.g., Okta, Auth0, your web server) that will be used in OAuth2.0 Token Exchange auth flows. See On-Behalf-Of Token Exchange for more details. |
- cURL
- Node.js
- Python

